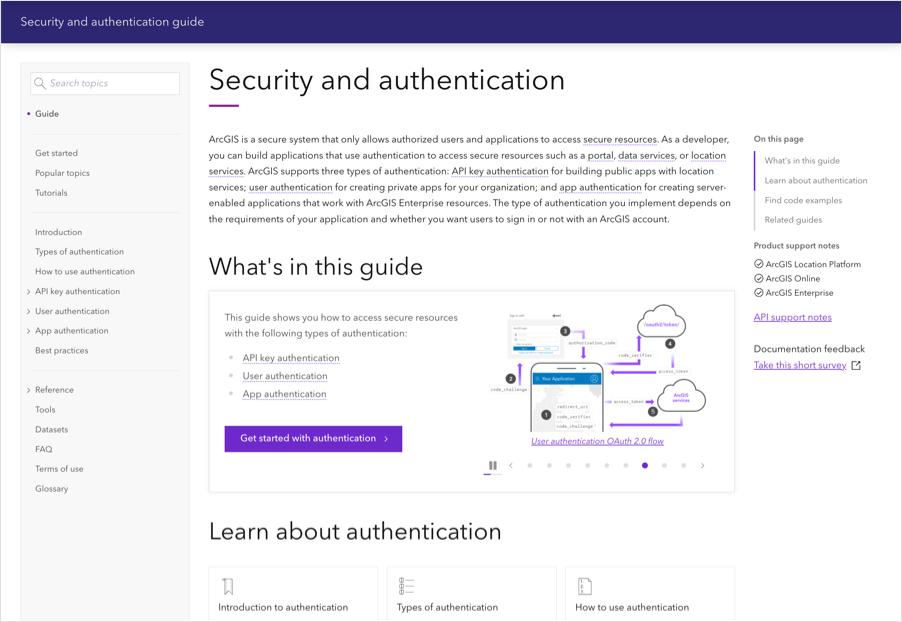
Earlier this year we released a new Security and authentication developer guide. This article takes a look at what’s inside the guide and at some of the key resources that will help you learn how to implement authentication for your applications.
Who is it for?
The new Security and authentication guide is an essential resource for all developers using ArcGIS technology to create custom applications. It is for any developer who has ArcGIS Location Platform, ArcGIS Online, or ArcGIS Enterprise. Setting up authentication is always a prerequisite for accessing ArcGIS resources, so regardless of whether you intend to use Location services, Spatial analysis services, the Portal service, or anything else, you’ll be making a pit stop in the authentication guide.
What’s inside?
The security and authentication guide contains everything you need to know about authentication with ArcGIS, from the basic concepts to advanced implementations.
The guide begins with Introduction to security and authentication, a page that explains the fundamentals of what authentication is and why it’s required in your applications. The Types of authentication and How to use authentication pages expand on the introduction, laying the foundation for the rest of the guide to come.
Types of authentication
Authentication with ArcGIS can take several different forms depending on the type of authentication you choose to use. The guide includes a chapter for each of the supported types of authentication:
Each chapter explains how to implement one type of authentication to access secure resources in ArcGIS. They also cover best practices related for implementing each type of authentication.
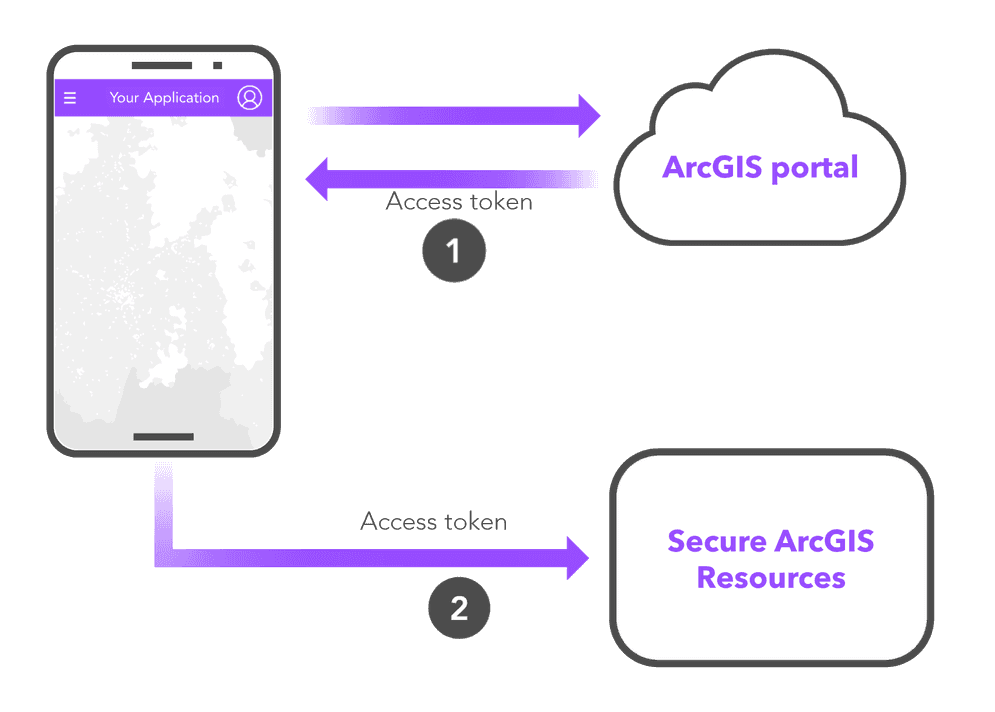
Tutorials for developer tools
In the guide you’ll also find a number of tutorials that explain how to use developer tools to help you implement authentication. For example, you’ll learn how to use the developer credential creator in your ArcGIS portal to create API key credentials and OAuth 2.0 credentials for your apps.
If you are ready to jump in, check out the tutorials related to API key authentication:
- Create an API key
- Migrate API keys (legacy) to API key credentials
- Manage API key credentials
- Rotate API keys
For a deeper dive, you can also learn how to create OAuth 2.0 credentials to set up user authentication and app authentication:
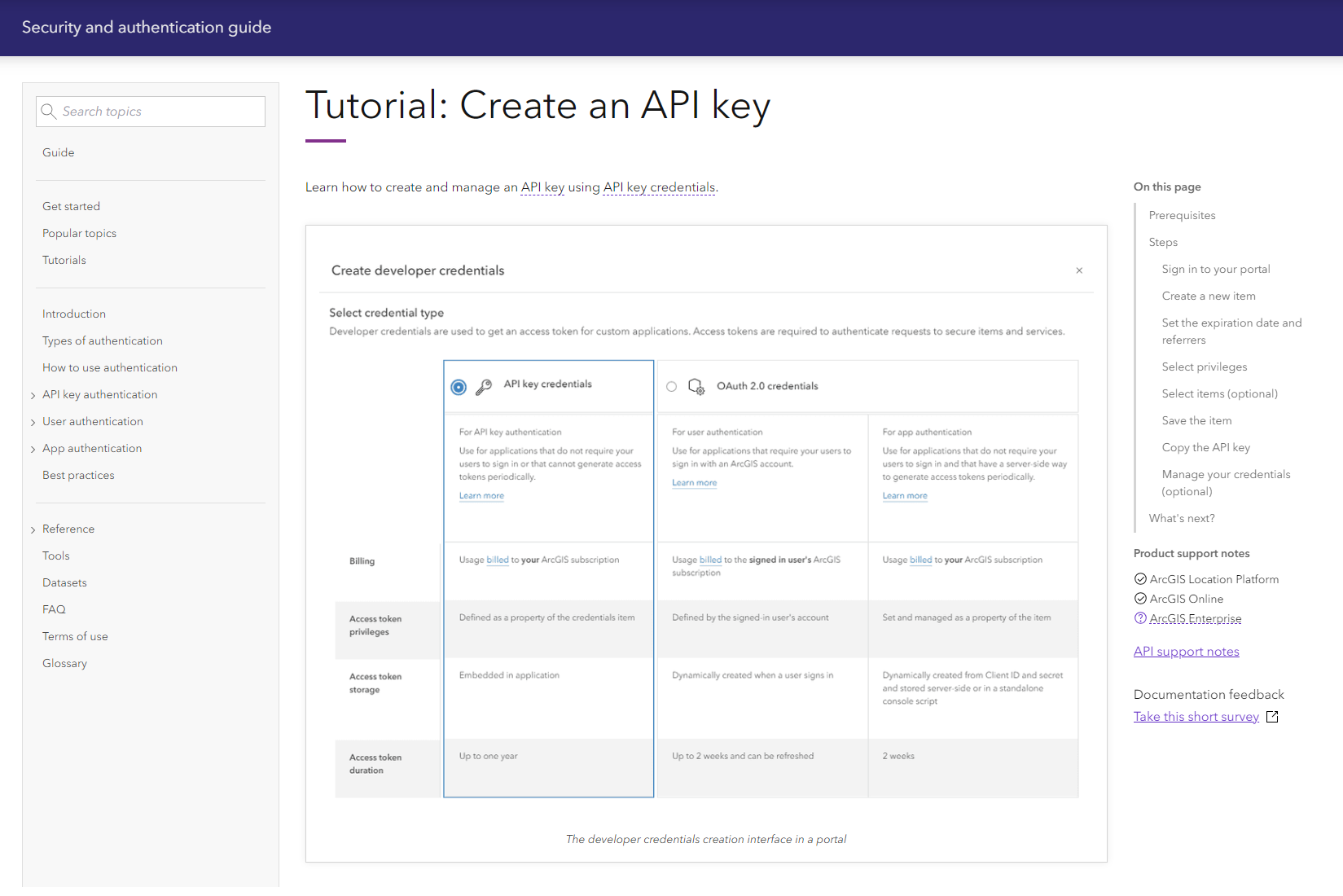
Workflows for every authentication method
In addition to tutorials for developer tools, the guide explains how authentication works on a technical level. In particular, the user authentication chapter provides a deep dive into how OAuth 2.0 user authentication works with ArcGIS.
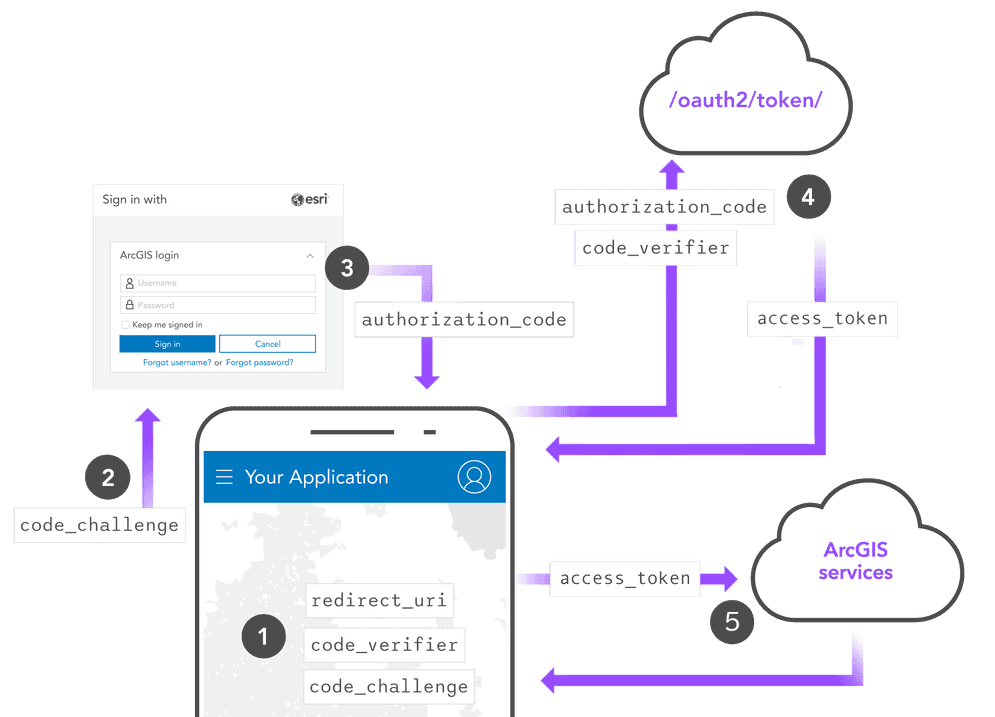
The user authentication flows section expands on this, explaining every supported workflow for user authentication in a dedicated page. For example, the commonly used Authorization code flow with PKCE has its own page that documents its OAuth 2.0 flow diagram and implementation details with ArcGIS.
Similarly to user authentication, the app authentication chapter explains the Client credentials flow with detailed implementation steps. It also includes links to Code examples hosted on GitHub.
…And more!
A few additional pages round out the rest of the guide, including detailed Best practices and FAQ pages that answer many common questions about authentication. The reference chapter also includes essential pages such as Privileges and REST authentication operations that you may find useful during development.
Ready to get started?
If you are ready to started, go to the Get started section of the Security and authentication guide, learn about the types of authentication, and start implementing authentication in your apps.
Once you implement authentication, you’ll be able to access many other services and resources offered by Esri, including location services, the portal service, spatial analysis services, and more.
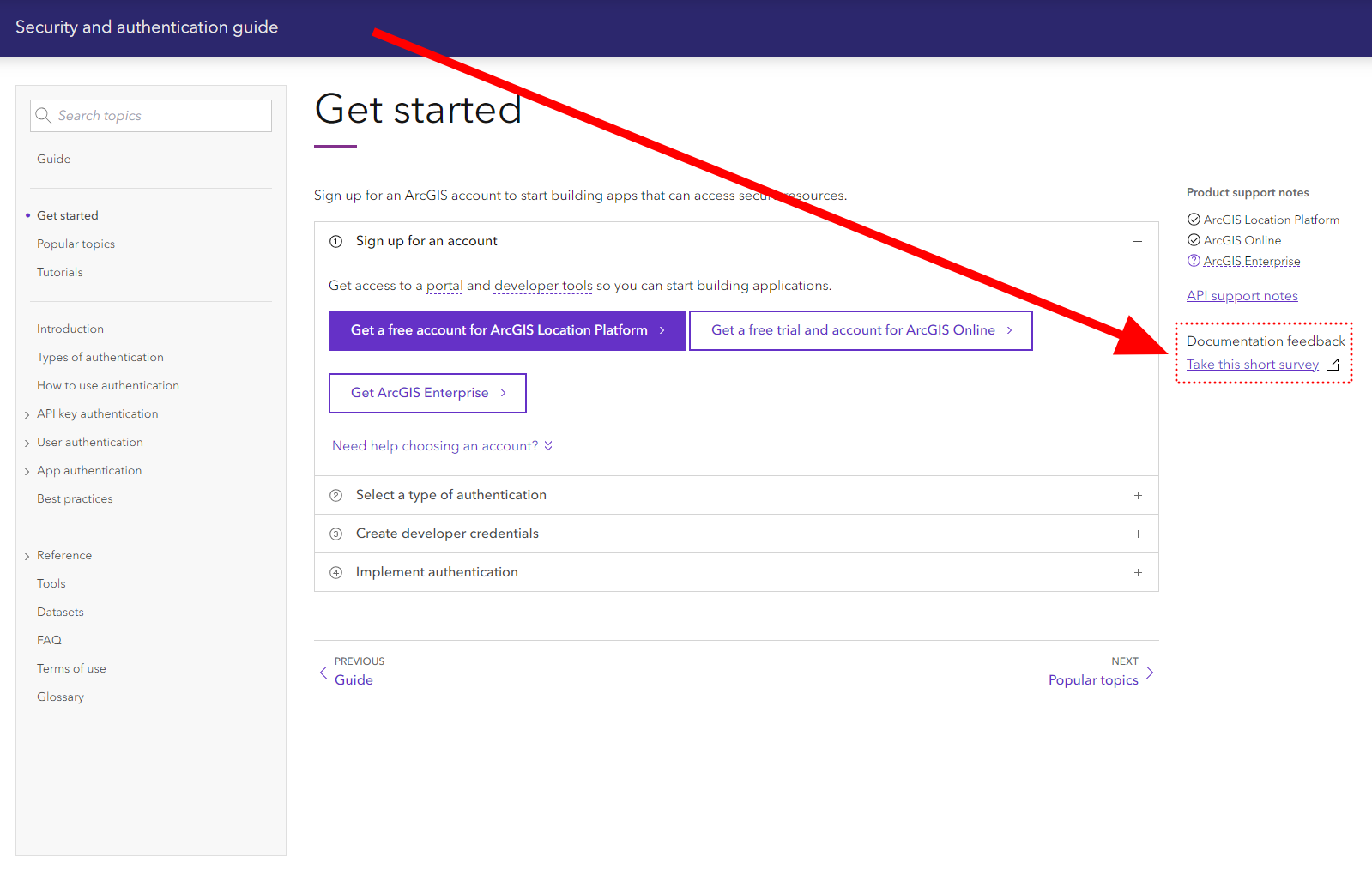
We want your feedback!
Please take our survey to let us know if the guide was helpful and how we can improve it.

G’day All
Not to detract from all the great work and just curious as to why the change with Non-Interactive Logins?
Thanks