Multifactor authentication (MFA) is a security measure that is highly recommended to protect your accounts and sensitive information. MFA provides increased security by requesting additional verification information when members sign in, such as a code obtained from an authenticator app.
By configuring multifactor authentication, you can significantly enhance your organization’s security by preventing unauthorized access even if someone manages to obtain login credentials. Multifactor authentication is an essential, often mandatory, part of your organization’s security needs.
This blog article focuses on configuring multifactor authentication for ArcGIS logins only. For other supported login methods, please check with your identity provider.

About organization logins
Your organization can be configured to allow members to sign in using a variety of methods, such as ArcGIS logins, Security Assertion Markup Language (SAML) logins, OpenID Connect logins, and social logins.
In the Logins section in the Security tab of your organization settings, you can set login options and reorder them. Click Show login screen to view the current settings.
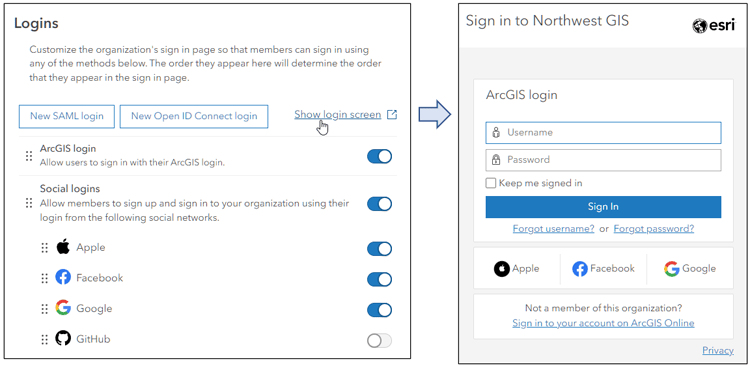
Organization settings for multifactor authentication are only for ArcGIS logins and can only be configured by administrators or others with sufficient privileges. Multifactor authentication for other methods other than ArcGIS logins must be configured via their respective identity providers.
For more information, see Configure security settings: Logins.

Enable multifactor authentication
In the Multifactor authentication section in the Security tab of your organization settings, you can Enable multifactor authentication for your organization.
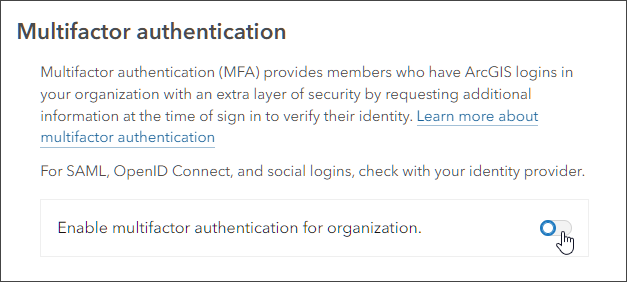
If you have not done so already, when you toggle multifactor authentication you will be prompted to designate at least two administrators who will receive email requests to troubleshoot members’ multifactor authentication issues. You can designate as many administrators as desired, ensuring that larger organizations, especially those covering multiple time zones, will have administrative help available if needed.
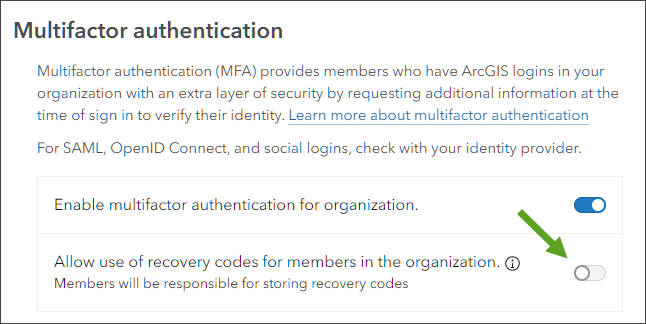
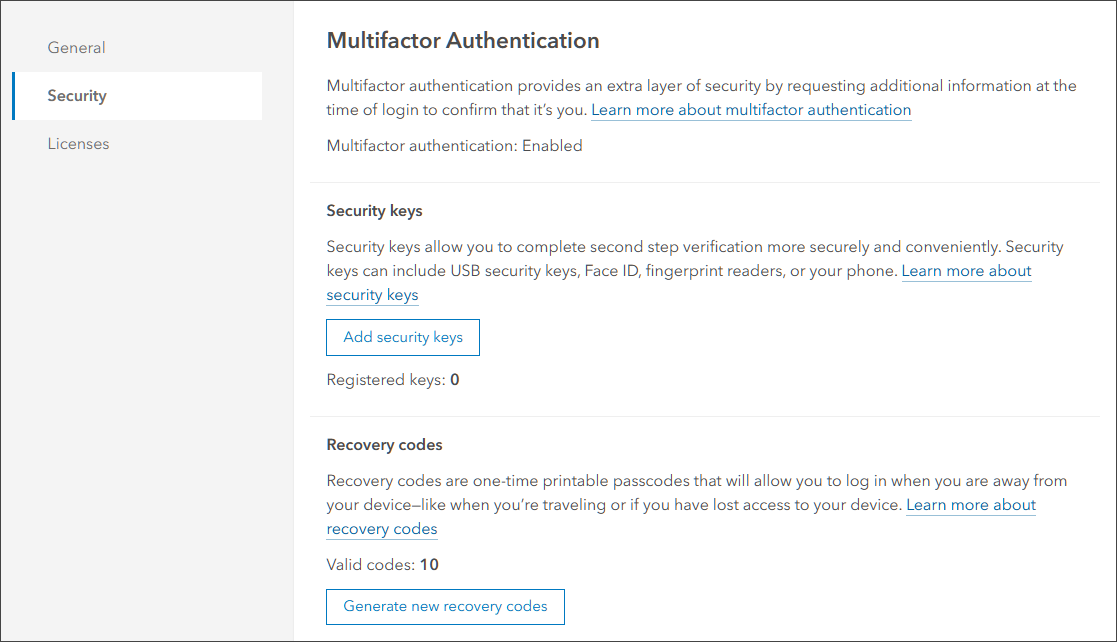
Once multifactor authentication has been enabled, you can optionally allow the use of recovery codes for organization members. Recovery codes are one-time use codes that provide second-step verification when members lose access to their authenticator app or security keys.
Without these recovery codes, members must contact organization administrators to sign in if their configured authenticator app or security keys are unavailable. Members using recovery codes are responsible for properly storing the information.
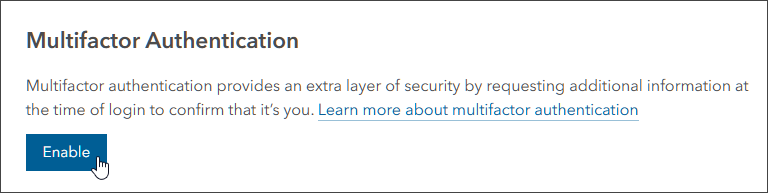
Once Enable multifactor authentication for organization is toggled on, multifactor authentication is optional for members using ArcGIS logins unless enforced (see section below). MFA can be configured by individual organization members if they choose to do so. This setting can be found in the Security tab in the member profile settings. Members can click Enable to set up multifactor authentication for their account.
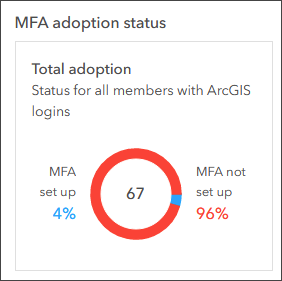
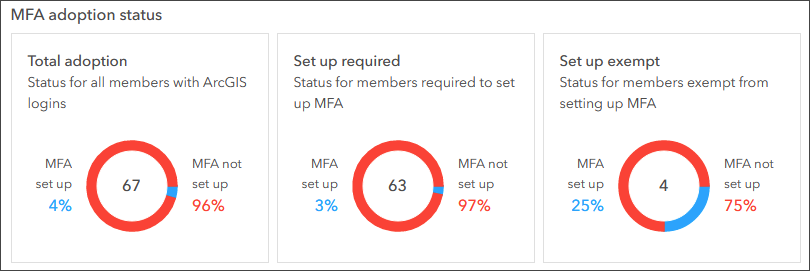
Once multifactor authentication has been enabled, administrators will see an MFA adoption status chart, showing how many members have set up multifactor authentication. This provides useful metrics for adoption and for moving forward with enforcement.

Enforcing multifactor authentication
Multifactor authentication provides the highest level of security when it is enforced throughout your organization. Enforcement will require all members with ArcGIS logins to adopt multifactor authentication when signing in. Once you enable multifactor authentication you will see an option to enforce it, as well as an option to create a member exemption list that removes listed members from enforcement.
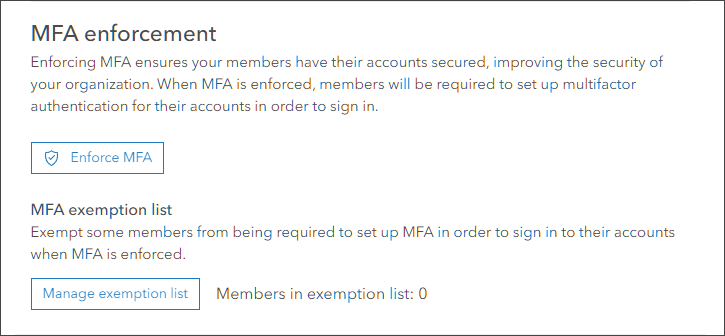
Click Enforce MFA to enforce multifactor authentication for ArcGIS logins.
An information pane will display, underscoring considerations and the immediate implications of multifactor authentication enforcement.
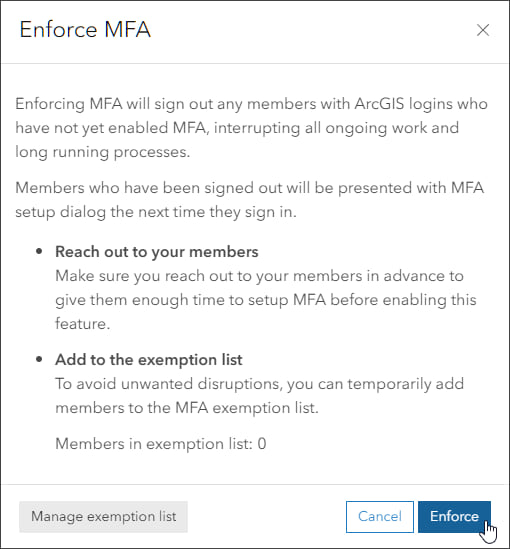
Things to consider:
- All currently signed in members using ArcGIS logins that have not configured MFA, whether they are administrators, field data collectors, or other members of your organization, will be forced out and will need to sign in again using multifactor authentication.
- When members sign in again, they will be required to use a Time-based One-Time Password (TOTP) authenticator app, such as Okta Authenticator, Google Authenticator, Microsoft Authenticator, or others to set up MFA.
If an exemption list has been configured, additional charts will be displayed, enabling you to track MFA adoption and showing the current status for required and exempt members.
Since this option circumvents multifactor authentication, it should be used only when special circumstances exist. For example, when a member needs additional time to procure and set up a device, is out in the field and does not have the means to set up MFA, and so forth.

Member experience when multifactor authentication is enforced
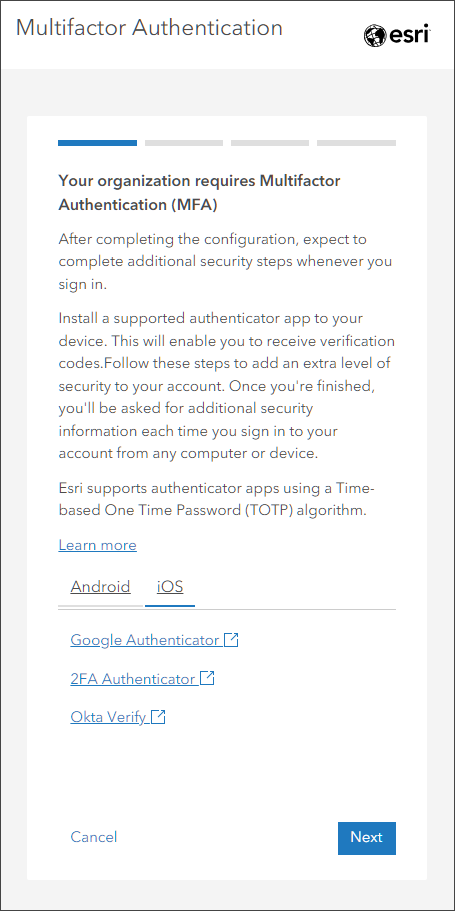
When multifactor authentication is enforced, all members using ArcGIS logins will need to use multifactor authentication to sign in to the organization. Members currently signed in with ArcGIS logins that have not set up MFA will be signed out immediately. All members using ArcGIS logins that have not set up multifactor authentication will be guided through the setup process the next time they sign in, and will need to have access to a TOTP authenticator app for completion.
Note that current activities, such as field data collection, map authoring, analysis, and other work may be interrupted. Best practices for ensuring minimal disruption of organization activities are listed in the best practices and considerations section below.
Members with ArcGIS logins signing in again after multifactor authentication has been enforced will see the following message:
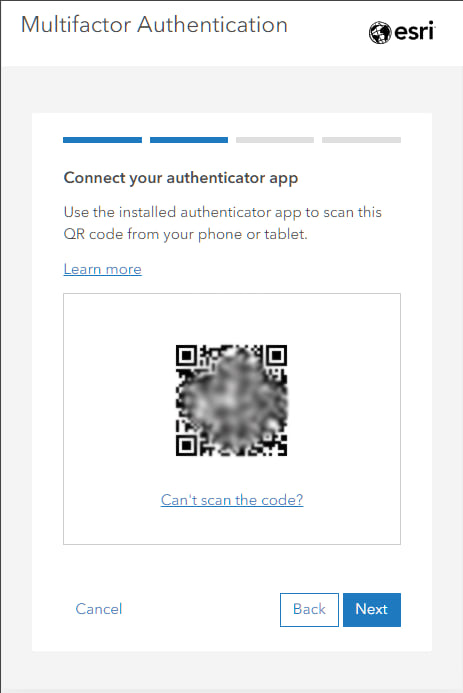
Those signing in for the first time after enforced multifactor authentication will be presented with a QR code, used to configure the authenticator application. Use your camera via the authenticator app to complete the configuration.
Once configured, the authenticator application can be used to generate the required code, providing secure sign in access.
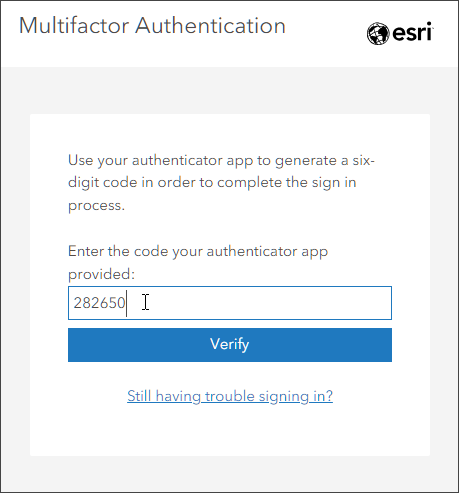
After successfully entering the security code, if the option to Allow use of recovery codes for members in the organization has been enabled, members signing in for the first time will be prompted to save the recovery codes (which they must acknowledge) and optionally register a security key.
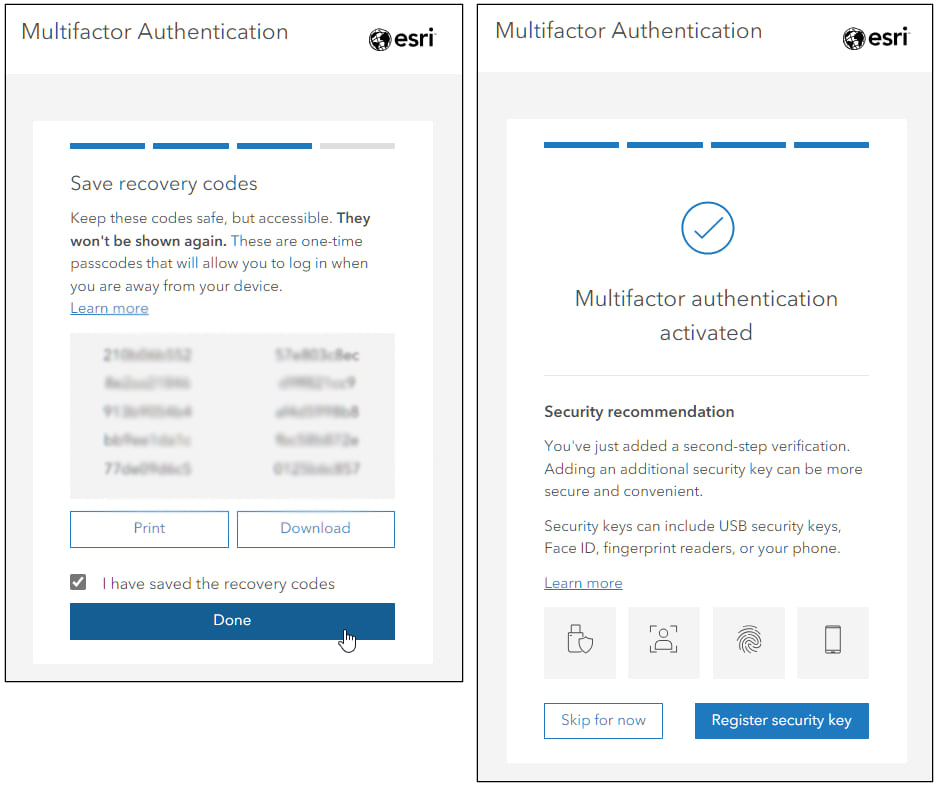
Security keys include USB devices, face recognition, a fingerprint, and other options. Security keys can be used as a second factor during authentication, following the first factor of a valid username and password.
Members are highly encouraged to configure one or more security keys. Security keys are considered the best choice for preventing phishing attacks, also reducing the time for members to authenticate.
Members can also go to the Multifactor Authentication section of their Security tab in their member profile settings to obtain recovery codes or register security keys for the second factor.

Best practices and considerations
When implementing multifactor authentication, the following are suggested:
Test the waters
If you are unsure about the impacts of multifactor authentication across your organization, you can set it up without enforcing it, giving members the option to try it out and the ability to provide feedback. You can gauge adoption via the MFA adoption chart and once you’ve reached a threshold of adoption, can move forward with enforcing multifactor authentication.
Plan in advance
Plan ahead for multifactor authentication, especially if you will enforce it. Enforcing multifactor authentication will automatically sign out any members with ArcGIS logins who have not yet enabled multifactor authentication, interrupting ongoing work and processes including field data workflows and analysis workflows.
To avoid unwanted disruptions, you can temporarily add members to the multifactor authentication exemption list. Members may also be unfamiliar with how MFA works and may need some time to install an authenticator app. Forward planning will minimize any confusion and interruptions.
Communicate your plans
Communicate in advance your intention to implement multifactor authentication and provide a target date. You can leverage the Information banner and Access notice settings to get the word out to members using ArcGIS logins. These settings are found in the Security tab of your organization settings.
Note that information banners are visible to anyone, including visitors to your site. Access notices are only seen when members sign in, therefore may be the better choice. For more information, see Get the word out: Use information banners and access notices in your ArcGIS organization.
Offer TOTP app suggestions
A wide variety of TOTP authenticator apps are available. Organization members may be unfamiliar with the options, so coming up with suggestions (perhaps with the guidance of your IT department) will ease the confusion.
Ensure the highest level of security
Your reasons for implementing multifactor authentication are based upon a need or requirement to increase the security of your organization. With that in mind, enforcing MFA is the logical choice. So is encouraging members to use security keys. Adopting multifactor authentication is a major step towards increased security. Ensuring compliance and best practices for members is a worthy goal when it comes to security. Adopting multifactor authentication is a significant step towards increased security, benefiting both users and organizations.
More information
For more information, see the following:
- Sign in (Help)
- Configure security settings (Help)
- View your settings (Help)


Commenting is not enabled for this article.