As many ArcGIS Enterprise users can tell, the software is much more than just GIS and mapping. It’s truly an enterprise IT solution – meaning it is built not only on GIS principles, but IT principles as well.
When I started at Esri almost nine years ago within Technical Support, this is something I had to learn. I have a computer science background and only understood GIS at a high level. While I quickly learned about GIS through a multitude of channels within Esri, I noticed that many ArcGIS Enterprise users who called into Technical Support came from a GIS background. This meant they often hadn’t had to learn IT concepts within their role, and some of these IT-based topics they needed to understand as administrators of ArcGIS Enterprise weren’t intuitive to them. One topic that came up time and time again was authentication.
Through this blog, I hope to demystify authentication in ArcGIS Enterprise, whether you have a GIS background or a computer science background like me. This will include examples of supported authentication types, considerations for determining the best fit for your organization, and a bit about using tokens in ArcGIS Enterprise.
Quick Links
What is an identity store | Overview of authentication types | Security needs are growing | Summary
What is authentication
Authentication, is a critical component of security, as it helps protect your sensitive data and maintain the integrity of your GIS infrastructure. It is the process used to verify your credentials, to ascertain the identity of an application or user that is attempting to connect to a system. Once that identity is confirmed, an authorization process determines if the application or user has permission to access the requested resources like data, maps, or apps. You can reduce the number of user credentials that a user needs to manage by configuring a single sign-on experience to secure your organization’s resources. Instead of having separate credentials – usernames and passwords – to each individual system, a single central repository is used across many different systems and applications.
There are several methods of authentication available in ArcGIS Enterprise, each with its own set of advantages and use cases. Understanding these options and choosing the right one for your organization can significantly enhance your security posture, streamline user management, and improve your members’ experience using ArcGIS Enterprise.
Why authentication matters
Before we start to talk about the different types of authentication, we need to understand why it matters. In today’s digital age, securing your GIS data and web services is more important than ever. Protecting sensitive information is crucial to maintaining trust and operational integrity. Authentication plays a crucial role in this by ensuring that only authorized users can access sensitive information.
Think of authentication as an identity check at an establishment, like a hotel. You provide them with your ID, perhaps your driver’s license or passport, to validate who you say you are at the front desk. You’re provided with a room key that gives you access to only your one specific room. Just as you need to scan your key to enter certain areas of the hotel, such as the pool or gym, users need to verify their identity to access different parts of ArcGIS Enterprise. As data is becoming more and more valuable, it’s important to know who is responsible for maintaining access and how they do it.
What is an identity store
The concept of identity stores is fundamental to authentication. An identity store is where user accounts and credentials are managed or stored. It specifies how authentication occurs and how group membership is handled. There are two main types of identity stores: a built-in identity store and an organization-specific identity store. We’ll dig into more specific definitions and details of each identity store later on.
ArcGIS supports integrating with several centralized identity standards including but not limited to the following:
- Security Assertion Markup Language (SAML)
- OpenID Connect (OIDC)
- Lightweight Directory Access Protocol (LDAP)
- Integrated Windows Authentication (IWA)
Based on the identity store(s) your organization uses, authentication and authorization may require specific technology configurations to enable access for users and applications to system resources.
Overview of authentication types
ArcGIS Enterprise is deemed enterprise-ready for several reasons, one of which is its support for various authentication methods. This flexibility allows your organization to select the most suitable option for them. Thinking back to the hotel example, your hotel key could be a physical key, a keycard, or a digital key on your mobile phone – the choice depends on what the hotel determines is best for them and their guests.
These are the main types of authentication options offered within ArcGIS Enterprise:
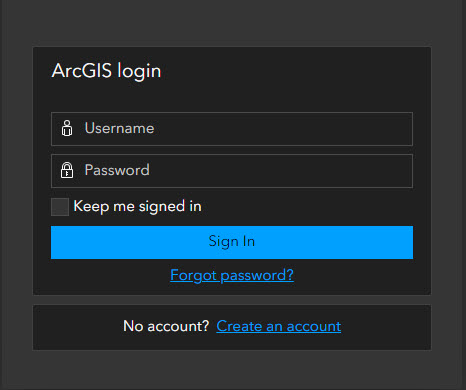
- Built-in identity store: This is the default authentication method in which user accounts are created directly within the ArcGIS Enterprise. It stores usernames, passwords, roles, and group memberships within ArcGIS Enterprise itself. This method is most commonly used for initial setup, development, and testing. The usernames and passwords are specific to each ArcGIS Enterprise deployment and won’t be found elsewhere.
- Organization-specific identity store: Organization-specific identity store: With this method, you can integrate with your organization’s existing identity management systems. Identity Providers (IdP) allow users to log in using their existing organizational credentials, which simplifies management and enhances existing security policies. This means you can potentially use the same username and password to access ArcGIS Enterprise that you use to sign into your computer or to access Microsoft Outlook. Some examples of different supported identity stores:
-
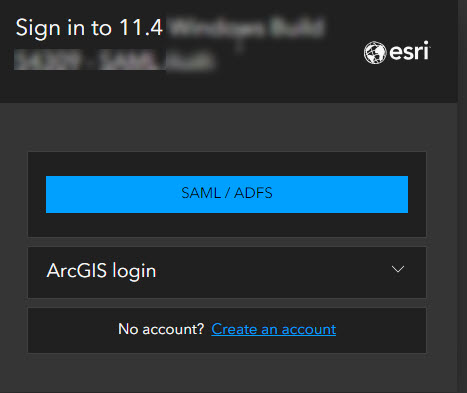
- Web-tier Authentication: This method uses web servers to handle authentication before users access the ArcGIS Enterprise. An example is Integrated Windows Authentication (IWA). In a Windows environment, users are automatically signed in to the ArcGIS Enterprise portal using their Windows credentials, providing a seamless experience.
- LDAP (Lightweight Directory Access Protocol) or portal-tier: To enable ArcGIS Enterprise access using both organization-specific and built-in identity stores without relying on SAML, you can implement portal-tier authentication. This involves configuring ArcGIS Enterprise with your Active Directory or LDAP identity store and enabling anonymous access in Microsoft IIS or your Java application server. For LDAP, you have the option to set up either portal-tier authentication or web-tier authentication using the ArcGIS Web Adaptor (Java Platform) deployed on a Java application server. Note that ArcGIS Web Adaptor (IIS) does not support web-tier authentication with LDAP.
- SAML (Security Assertion Markup Language): SAML is an open standard that is used to securely exchange authentication and authorization data between an organization-specific identity provider and a service provider (in this case, ArcGIS Enterprise is the service provider). SAML is supported by a wide variety of identity providers.
- OIDC (OpenID Connect): OIDC is also an open standard supported by many identity providers. ArcGIS Enterprise supports the OpenID Connect authentication protocol and integrates with IdPs such as Okta and Google that support OpenID Connect. You can configure your organization’s sign-in page to show only the OpenID Connect login or show the OpenID Connect login along with ArcGIS login and SAML login (if configured).
If your ArcGIS Online and ArcGIS Enterprise organizations use the same SAML-compliant or OIDC identity provider, you can match organization-specific usernames. This will provide a single sign-on experience to users of both systems, but it is important to keep in mind that ArcGIS Online and ArcGIS Enterprise still represent separate organizations with their own user accounts, permissions, groups, and content. Signing in to ArcGIS Enterprise will not display the same content as ArcGIS Online even though users may have logged into both systems using the same credentials.
Security needs are growing
Authentication methods within enterprise software are crucial for ensuring secure access to sensitive data and information. These methods include password-based authentication, which is the most common, but are increasingly supplemented by more secure options like multi-factor authentication (MFA). MFA adds an extra layer of security by requiring users to provide two or more verification factors, such as a password and a code sent to their mobile device. Using a centrally managed identity provider allows organizations to use their standard processes for managing user credentials, including MFA requirements, and making it easier for their users to access ArcGIS Online and ArcGIS Enterprise in the same way that the log into any other business system.
Summary
It is important to choose an authentication option that aligns with business, security, and compliance goals. Commonly used methods for security and ease of use include SAML and OIDC. By understanding how other enterprise IT systems are managed within an organization and leveraging existing authentication solutions, an informed decision can be made.
For more detailed information, examples, and guidance, be sure to visit the ArcGIS Architecture Center.

Article Discussion: