Threat actors in cyberspace often work indiscriminately to expose and exploit vulnerabilities; these crafty adversaries can compromise, infiltrate, and exfiltrate your most guarded secrets. Information gathered on your cyber pattern of life (PoL) can be used as leverage in malicious ways and the challenges that each individual and organization continues to encounter in the face of an ever-evolving cyber threat grow in complexity daily.
As teams actively pursue creative methods to mitigate the consequences inflicted upon our communities from cyberattacks, new advances in technological surveillance, detection, and analysis continue to serve as a force multiplier for many outnumbered, task-saturated crews charged with its protection. Adversarial tactics, techniques, and procedures (TTPs) are captured and studied to ensure defense strategies are in place and evolve with threat complexity. Cyberattacks represent a new brand of guerilla warfare whose unfamiliar operational space is constantly being used against us. We must consider new approaches as the consequences of underestimating this threat could bring considerable damage.
ArcGIS AllSource adds an incredibly robust, extensible analysis capability to support the ongoing efforts surrounding cyber threat intelligence. AllSource can be used in all phases of the Cyber Threat Intelligence Cycle, while leveraging advanced analytics of the ArcGIS Enterprise from backend servers like the Knowledge Server, to identify threat vectors and deploy mitigation strategies to protect an organization’s cyber infrastructure.
Direction:
Before we can develop and implement our threat intelligence strategy successfully, it’s essential to identify what it is we’re setting out to protect in the first place. An organization’s priorities can be captured in ArcGIS AllSource as the starting point for the cyber security program to grow. A clear, specific understanding of the potential impacts to any level of compromise and their role in its prevention is required by all Stakeholders within an organization. In today’s business spaces, our ability to turn data into a competitive advantage is the difference between thriving as a business and shuttering the doors. Ensuring that all Team members understand the organization’s key priorities allows for highly responsive defense in response to or preventing an attack.
Collection:
ArcGIS AllSource, as the name would imply, is born for all-source data fusion and holds that as one of its critical functions to ensure analysts can visualize and perform robust analysis workflows on that data to support informed decision making.
For cybersecurity professionals, collection often comes from open-source intelligence (OSINT) outlets like social media where insights can be gleaned from threat actors touting their skills, or communities of practice using the medium as a common communication pipeline to discuss current cyber activities and trends. Suppose a cyber analyst detects activity based around a certain threat vector like a right-to-left override. In that case, ArcGIS AllSource can be utilized to further investigate and set in motion a series of steps to ensure preemptive mitigation of such an attack. Mapping in data sources like the MITRE ATT&CK framework allows analysts to begin layering information that can be used to extract insights on a particular situation.
Processing:
Once our data sources are mapped successfully and information flows into AllSource, it’s often necessary to prepare the data, normalizing it for use within the Enterprise.
ArcGIS AllSource has many tools to help us normalize and clean our data. The MITRE ATT&CK dataset has many ways to access the data, such as a JavaScript Object Notation file (JSON), a Python library, and a Microsoft Excel workbook. We will start by downloading the Microsoft Excel workbook and using this to create our necessary products.
The Excel Workbook comes with many sheets, including fields we can clean up to gain more insight into our analysis. First, we can import each of these sheets into a mobile geodatabase to get the correct field types and allow for a more robust analytical experience. Converting these sheets to a table in a mobile geodatabase is quite simple; we only need to right-click on the sheet and export our data.
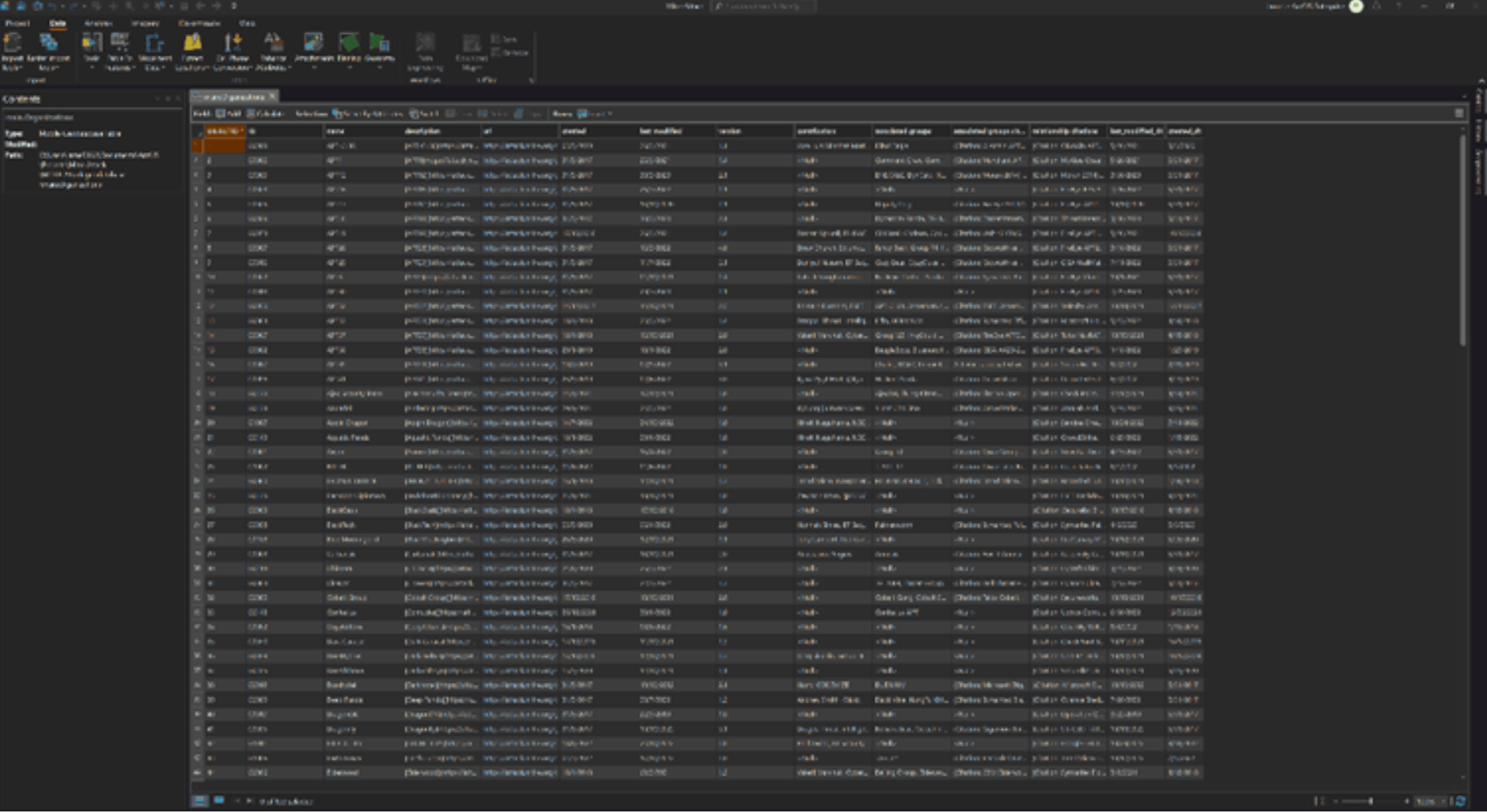
Once that is complete, we can adjust some of the field types. One thing we can do is change the Created and Last Modified fields that are present in each table from text fields to date fields. ArcGIS AllSource includes many tools to help you clean your data, including the useful Convert Time Field; this tool allows you to convert many field types to a date field or any other field type of your choice.
Analysis and Production:
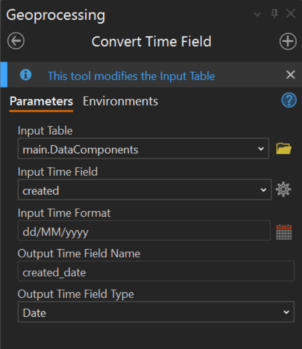
Now that the data is prepared for use, we can leverage the advanced analysis functionality provided by the backend ArcGIS Knowledge Server deployed within the Enterprise to provide additional understanding about the right-to-left override threat vector we’d encountered.
After hearing that a right-to-left threat vector had been employed recently, we can drill down into the data to further understand the number, cadence, and location of similar attacks that have been reported over a specified period. With a substantial uptick of use in a particular area, we can leverage additional insights from social media to see increased negative rhetoric from threat actors out of a specific region. Expanding the resultant knowledge graph displayed in AllSource from the MITRE ATT&CK dataset, we can find a handful of organizations that are particularly prone to this kind of attack. Selecting the organization, Entity1, we learn this is a terror organization.
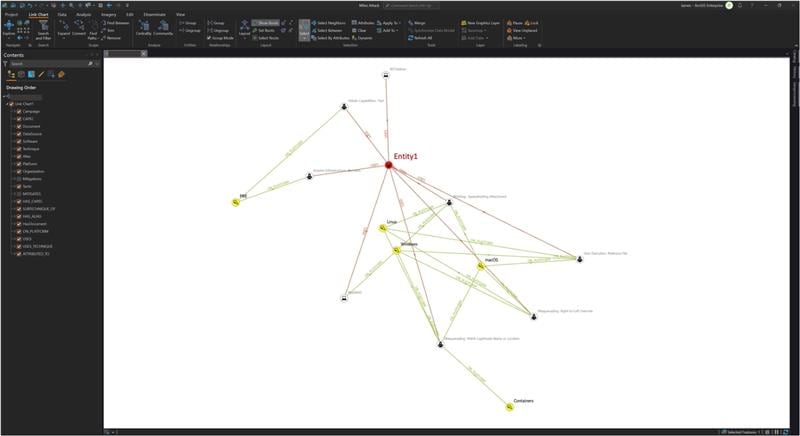
Entity1 is known to utilize additional threat vectors in their attacks. Using AllSource, we can identify such attacks and drill down on their mitigation steps. Seeing that this particular organization matched well with the description of activities found in our OSINT collections, we could recommend to leadership with a marked level of confidence that deploying the steps involved with mitigating the effects of such an attack could increase our security posture in the face of such an adversary.
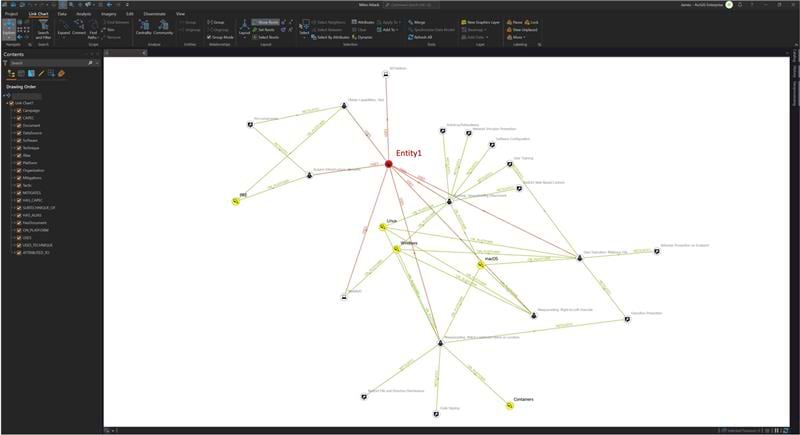
Once all the relevant data has been collected, we can export each relevant field to .png files to support a final product consisting of our recommended way forward. This will provide all the relevant stakeholders/decision makers with the full scope of the current operational landscape.
Dissemination:
Now it’s time to share the information with those critical stakeholders. This is done seamlessly through various methods/formats shown here under the “Dissemination” heading on the AllSource ribbon bar. The cybersecurity teams will move out from decisions made to ensure mitigation actions are set in place, any additional preemptive measures necessary to prevent or insulate the architecture from follow-on attacks are implemented.
Feedback:
Finally, an analysis of the efficacy of our defenses to prevent an attack or lessen its severity is necessary to ensure that our security posture evolves with the threat itself. In a post-reflection session, stakeholders can use ArcGIS AllSource to capture critical insights and adjust mitigation steps accordingly to ensure any new requirements in defensive tactics are captured and cataloged. This continued refinement of tactics to defend organizational priorities is an ever-evolving process to posture your team best for combat against threat actors looking to impose their will.
The sheer volume of data supporting cyber threat intelligence can be overwhelming. Making sense of that data by extracting insights and bringing context to activities in the space is where you’ll see ArcGIS AllSource excel to reach its fullest expression of capability. The sophisticated threat lurking in the shadows requires a great deal of planning, intimate knowledge of the tools at hand, and domain expertise by your cyber security cadre to challenge properly. AllSource allows organizations to move forward confidently, prepared to engage and protect what is most valuable.
To learn more about ArcGIS AllSource contact your Esri representative.




Commenting is not enabled for this article.