It had been a volatile year at the Dallas office of a national insurance company. Tornadoes had ravaged the area in spring. Then a hailstorm marred an idyllic summer, smashing windshields and denting roofs. As summer faded, nature grew calm again. In the claims department, calls leveled off and adjusters cleared their backlog. The manager was keeping normal hours again.
But then, in early September, a raft of homeowner claims appeared, all involving roof damage from the hailstorm three months earlier. On its own, the time delay wasn’t a red flag; the claims manager knew that homeowners often noticed damage when they cleaned their gutters in the fall. But the volume of claims was perplexing—a dozen in three days.
To the manager, something seemed amiss. Technology confirmed it.
She began to explore the claims, plotting each address on a map in the company’s geographic information system (GIS). On top of those addresses, she overlaid data from the National Weather Service, which had tracked the hail on the day in question. Nine of the addresses had been directly in the storm’s path. But three of the houses had experienced no hail that day.
The information was definitive—three of the properties had no business receiving a payout for damage claims—but a mystery remained: why had a dozen claims appeared in a three-day period, three months after the storm? The answer came from a conversation with one of the homeowners affected by hail. As it turned out, a contractor had knocked on their door the prior week, mentioning the hailstorm and suggesting they might have roof damage they didn’t know about. (The contractor also left a business card touting expertise in roof repair.)
Of the three homeowners who hadn’t been hit by hail but had filed claims, one or two might have made an innocent mistake. Perhaps they’d been out of town on the day of the storm and misattributed roof damage to the hail. But the chances were good that at least one of the three knew they hadn’t been hit by hail and sensed an opportunity for free repairs on unrelated damage. The GIS technology didn’t explain anyone’s motivation. But it did give the insurance company enough evidence to make an informed decision and avoid paying out on a possibly fraudulent claim.

Companies purchase insurance to cover many aspects of their business, but often neglect to take action to protect themselves against fraud.
What the claims manager knew—and many companies overlook—is the fact that fraud, like poker players, can have a tell. It often leaves footprints in specific locations, like the homes where owners claimed hail damage. And those clues are easiest to trace when viewed on a map or in a visualization.
Thus a best practice for addressing fraud—in the insurance industry and elsewhere—is early detection through GIS technology. This immediately puts fraud schemes in check, reduces payouts, and saves time spent on follow-up investigations.
An Unmistakable Impact
Every day, fraudsters are probing companies from within and without. Some are inflating expense reports, while others are hoping their phony invoices will sail through accounts payable unremarked. The most brazen are hatching embezzlement schemes that could threaten a company’s future.
Their impact cannot be dismissed. In 2016, more than 23 percent of occupational fraud cases yielded a loss in excess of $1 million, according to a study by the Association of Certified Fraud Examiners (ACFE). Over the course of a year, ACFE estimates that the average company loses 5 percent of its revenue to fraud. Add to that the growing prevalence of online fraud, and the challenge grows even more significant.
Some companies consider fraud the cost of doing business—something you clean up after, rather than prevent. That thinking could stem from corporate laziness, but more often, it owes to the impression that fraud is too hard to detect.
To an extent, that has become a self-fulfilling prophecy. Today, a high percentage of fraud cases come to light through decidedly old-fashioned channels, according to the ACFE report. In 2016, the most common of those was a tip—4 in 10 occupational fraud cases were detected that way. Only 17 percent were discovered by auditors. Technology plays an even smaller role, according to researchers at KPMG, who wrote this in a 2016 report:
“Proactive data analytics, searching for fraud amid anomalies and suspicious business activity, accounts for only 3% of frauds detected.”
At that rate, a company might as well wait for a confession—1.3 percent of cases are reported by the fraudsters themselves, according to the ACFE.
The Foundation of Fraud
Each industry is prone to certain types of fraud. Manufacturers, for instance, are hit hardest by corruption, billing scams, and noncash threats, while insurance companies face corruption, skimming, and check tampering. (For a full look at industry-specific fraud, visit the ACFE report.)
Although fraud’s complexion varies by industry, evidence of any kind of fraud often shares a characteristic: geography. With that, businesses can leverage technology—often technology that’s already used in other areas of the company—to ferret out fraudulent activity.

Fraud, like poker players, can have a tell. It often leaves footprints in specific locations, and those clues are easiest to trace when viewed on a map or in a visualization.
No single technology detects all instances of fraud, but a geographic information system (GIS) serves as the hub of many companies’ efforts. With the help of data feeds from enterprise resource planning (ERP) or customer relationship management (CRM) systems, GIS can provide an enterprise-level view of operations and create intelligent maps that help managers track information anomalies to their source.
For executives looking to recoup the 5 percent of revenue they lose to fraud, technology delivers maximum return when it’s part of a fraud risk management plan. Such a plan employs human intuition, integrated systems, data management, and analytics to spot data anomalies and predict risk.
The plan rests on three tenets: prevention, detection, and response.
Prevention
To begin an assessment, fraud managers should list risk factors that are relevant to their business. Most industries have established lists of anomalies to watch for.
For instance, along the path that turns raw materials into finished goods, certain supply chain activities are common targets of fraud. Inventory loss and expense reimbursement, counterfeit products and stolen equipment—these incidents occur time and again. Fortunately, most supply chain transactions have traceable digital elements—vital clues for preventing unwelcome activity.
Once a company establishes which areas of the supply chain to police, technology can do its work. The manager can populate GIS with maps of previous incidents and use GIS modeling tools to identify locations with similar physical and environmental characteristics. That analysis helps managers recognize patterns, begin to understand the conditions that favor fraud, and take steps to prevent problems.
Detection
The next step in the plan is to create practices that detect fraud.
As the ACFE study notes, most fraud cases are detected by whistle-blowers. Companies can encourage tips by making reporting easier. For instance, the fraud team might create a lightweight GIS app that lets employees, contractors, and vendors report illegal activity through their mobile devices. Users can geotag a photo; add notes; and send it to the compliance team, which can cross-check the report with relevant data and analyze the evidence.
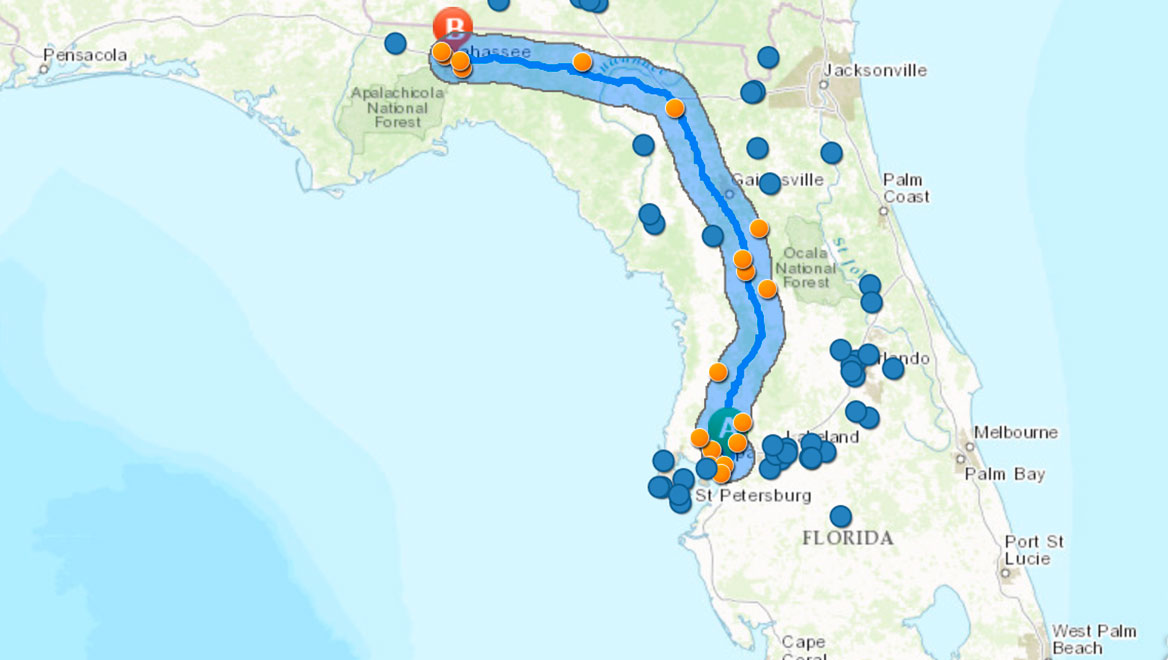
But detection can’t depend entirely on whistleblowers. Take the case of a national delivery business that used contractors to move packages along some midrange routes. Each contractor was issued a gas card for these trips, which could span hundreds of miles. When company managers used GIS to plot the gas purchases on a map (see image at left), they noticed that some were occurring more than 10 miles from the prescribed route. When they added the dollar value of transactions to the map, the areas of likely fraud lit up like beacons. In one case, inspectors nabbed a contractor that had racked up $5 million in fraudulent charges.
In the realm of detection, any of these conditions could indicate fraud:
- Inventory levels that spike even as sales orders remain steady
- A work crew with above-average incidence of lost tools or equipment
- A single vendor that uses multiple addresses for receipt of payment or goods
Like the delivery-business inspectors and the insurance claims manager, a good fraud detection team knows that these cases share one trait: they are all easier to detect when viewed on a map.
Response
In any industry, executives and managers can create parameters for all kinds of activity—from the dollar amount of transactions to the assigned work area of an employee. When those parameters are breached, a GIS tool can issue real-time alerts.
Thus begins the final phase of a fraud risk mitigation plan: the response.
The first step in a successful response is to document and investigate the conditions surrounding the incident. Companies can add security video, sensor data, and other evidence to a map for simple reference. All that information may eventually be used in court.
Once the investigation has run its course, successful companies convert what they’ve learned into better policies and communicate those updates to employees and partners.
In a perfect world, no company would need to spend time and resources fighting fraud. But in a world where an average of 5 percent of revenue is being taken off the top line, most companies would be ill-advised to simply watch it go.
The Esri Brief
Trending insights from WhereNext and other leading publicationsTrending articles
December 5, 2024 |
July 25, 2023 |
November 12, 2018 |

April 1, 2025 |

February 1, 2022 |

April 29, 2025 |