For any IT manager thinking about putting off an important security patch, here’s a seven-figure prompt: The average cost of a cyberattack more than doubled last year to $1.85 million, according to Allianz Global Corporate & Specialty, which began covering cyber insurance claims in 2013.
The protective value of IT patching is well-known, but the practice is too often neglected.
In November, President Joe Biden ordered most federal departments to patch long-lingering vulnerabilities and update outdated software systems to strengthen them against attacks.
Preventative patching isn’t solely a government concern, though.
It took less than a week after US authorities warned of a vulnerability in a password management application for at least nine companies to be compromised, according to IT World Canada, a cybersecurity industry publication. The companies hadn’t installed a needed patch. The lesson: act quickly.
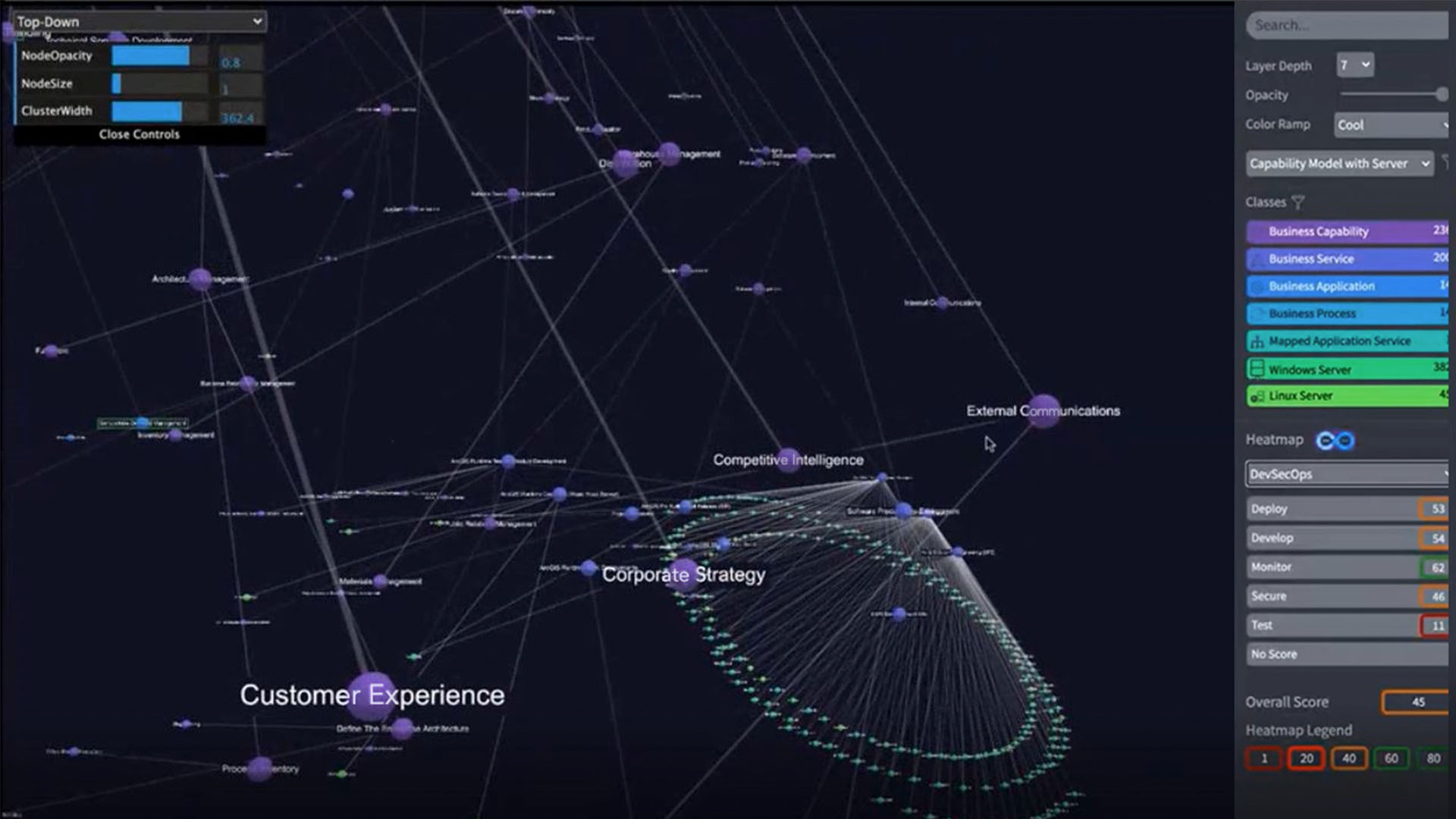
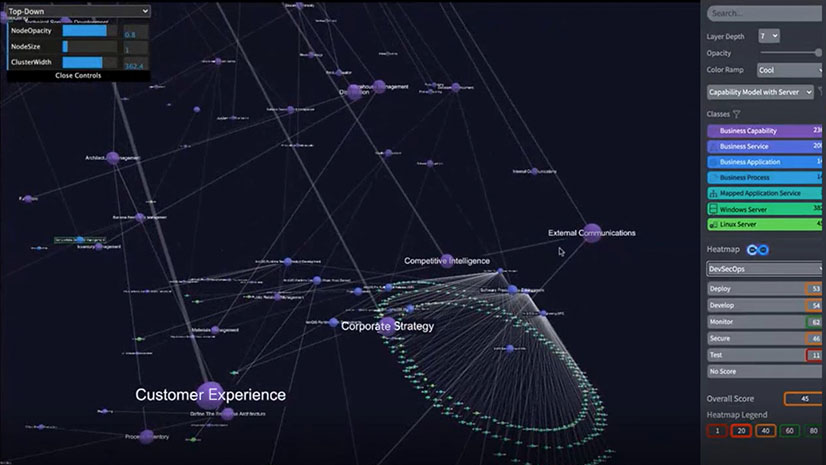
One way for corporate CIOs and risk officers to start improving their defenses is to map a company’s IT infrastructure, including every connected device, its relationships to other systems, its patch status, and even its physical location.
With an IT map, CIOs and IT decision-makers can pinpoint vulnerable servers, software, and devices, and bolster the chances of preventing an attack.
Threats Persist
Cyberattacks are hardly slowing. More than one in three organizations reported an increase in cyberattacks in 2020, according to a survey of IT professionals conducted by ISACA. One recent notable victim of corporate ransomware was Colonial Pipeline, which temporarily shut down all of its gasoline pipes after hackers infiltrated its system and demanded a $4.4 million ransom. Hackers caused a cascade of headaches for Kaseya, a technology management provider, and its customers—ransom demands exceeded $5 million in some cases. In March, Microsoft warned that unpatched Microsoft Exchange Servers had been compromised by DearCry ransomware before it could be detected and stopped. More recently, the widespread Log4j vulnerability has sent IT leaders scrambling to update systems for email, web applications, cloud computing, and more.
In these scenarios, bad actors often sneak in through system vulnerabilities before the affected organizations identify their weak links and address them. Setting up digital guardrails in advance, by protecting a network from those intent on causing damage, can help.
That begins with understanding one’s network by inventorying and mapping every device, server, switch, and connection, then visualizing them all.
A Patch of Prevention with an IT Map
Knowing which IT assets have been patched and which haven’t is key. It can also be difficult to ascertain, especially for IT departments starved for cybersecurity professionals that have been in short supply.
An IT map can help by creating a single source of truth for the organization via a digital twin of an organization’s people, processes, and technology. This digital twin shows technology assets and human users across the network, and can be viewed as a simple line chart or a solar system showing the hubs and spokes connecting a company’s digital universe.
Geography adds another layer of operational awareness to an IT map. If an IT manager locates an unpatched server on the digital twin, the manager can click through to a digital map showing where that hardware resides—down to its precise location in a rack of servers.
When an IT map is paired with service management software, IT staff can request the installation of a patch from within the map. It’s not unlike the technology that helps utility workers identify and fix buried pipes and wires. The digital twin visualizes what might otherwise go unseen, helping decision-makers take informed action. Such tools encourage preventive maintenance—on underground pipes or unpatched servers—limiting costly and unnecessary repair work down the road.

One way for corporate CIOs and risk officers to start improving their defenses is to map a company’s IT infrastructure, including every connected device, its relationships to other systems, its patch status, and even its physical location.
A Watchful Eye on Age, Activity
Monitoring the age of IT systems is also a critical aspect of cybersecurity. In the government accountability reports that prompted President Biden’s directive, some agencies hadn’t updated their software in decades. That included the Department of Transportation, which was operating with 35-year-old software, and the Department of Education, where one application stored student loan data that was nearly 50 years old.
Installing the latest updates—complete with security patches—is important for both public and private enterprises. Managers can filter an IT map by device or software age, organizing the results in a way that makes it easier to track older devices and software susceptible to hacking.
Eliminating vulnerabilities and tracing security flaws also involves knowing who has physically accessed sensitive areas or devices. An IT map shows the locations as well as the specific employees who may have accessed areas like R&D labs or secure server rooms.
The IT map is useful beyond cybersecurity planning and response. An IT professional might track weather-related events like flooding or wildfires to understand their potential impact on the infrastructure underpinning a company’s network, and shift assets proactively.
In the unwelcome case of a successful cyberattack, having a detailed IT map allows network security professionals to trace the problem to its root, respond more quickly, and revive operations.
Mapping has long been a competitive differentiator in business, guiding leaders to choose the best storefront, teach suppliers sustainable practices, and manage fleets of employees and vehicles. Now, an organization’s IT infrastructure can be mapped, tracked, and better understood to prevent costly cyberattacks and speed recovery if they do occur.
The Esri Brief
Trending insights from WhereNext and other leading publicationsTrending articles
December 5, 2024 |
November 12, 2018 |
July 25, 2023 |

February 1, 2022 |

March 18, 2025 |

May 28, 2025 |