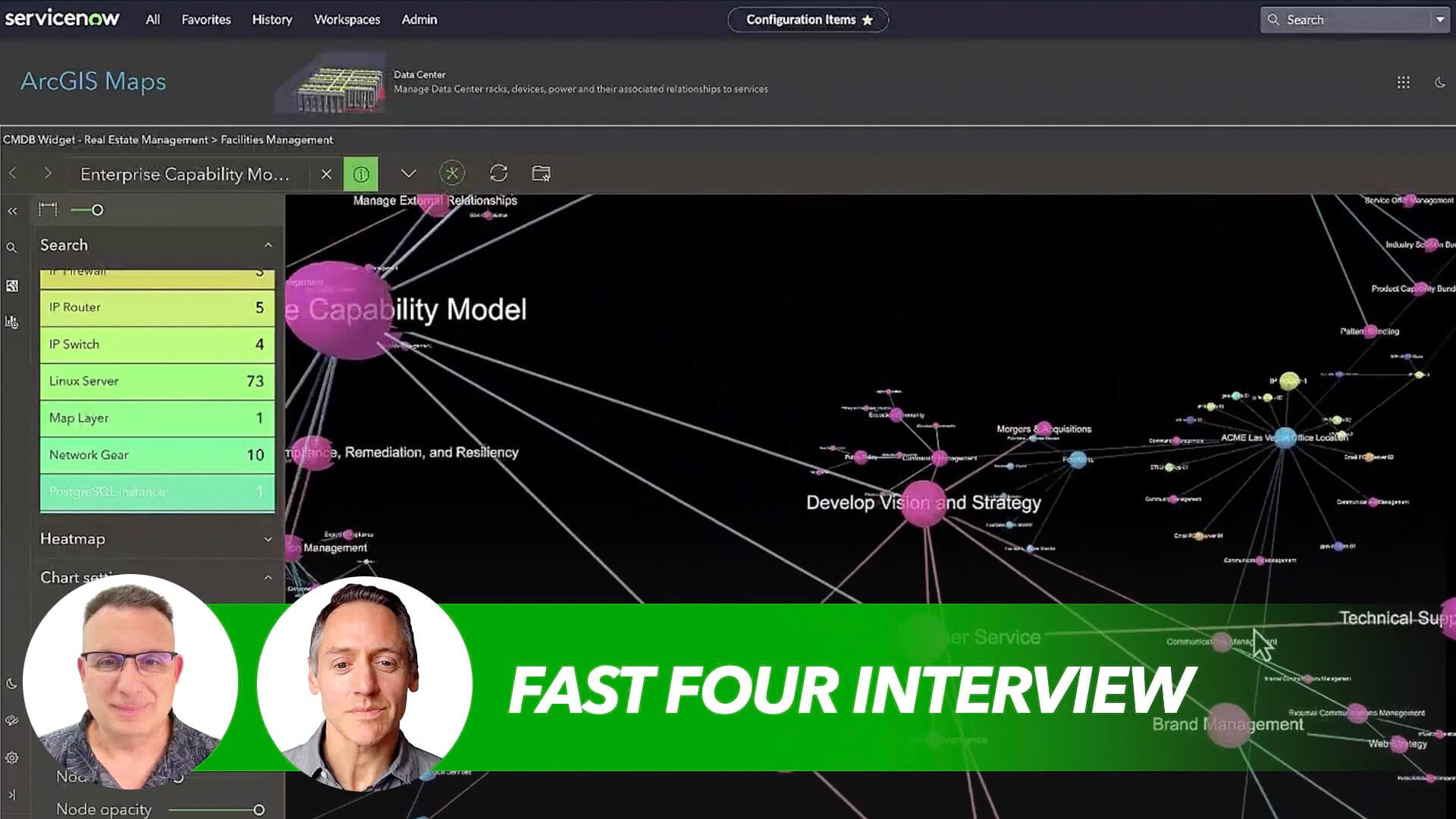
CIOs are chasing a holy grail—an effective way to visualize the organization as IT ecosystems grow increasingly complex. With third-party data streaming in, software apps proliferating, and security threats demanding constant vigilance, their challenge grows by the day.
There’s a map for that, says Dan Abushanab.
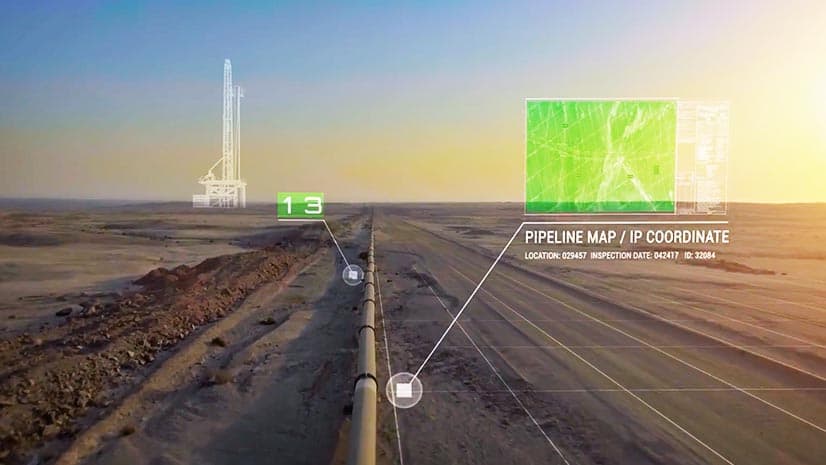
In this episode of the WhereNext Fast Four, Esri’s CIO discusses the IT map, an enhanced version of the configuration management database, or CMDB. With clear lines connecting a company’s people, processes, and technology, the IT map provides tech leaders a playbook for everything from implementing security patches to ensuring that employees don’t notice the IT infrastructure supporting their work.
In an IT world dominated by bits and bytes, a map may seem out of place. Through simple scenarios and captivating visuals, Abushanab demonstrates how reliable maps bring clarity and efficiency to CIOs, IT teams, and the entire organization.
Check out the video interview below, or read the transcript.
Chris Chiappinelli: Welcome, everyone, to the WhereNext Fast Four. We’re here to talk IT mapping. It’s a fascinating concept. It’s the centerpiece of one of the most popular WhereNext articles of all time. We are joined by Dan Abushanab who is something of an expert on the practice, so we are very excited to have him here on the Fast Four. Dan, this all starts with enterprise technology and how CIOs and business leaders can keep tabs on it. Can you explain the basic situation here?
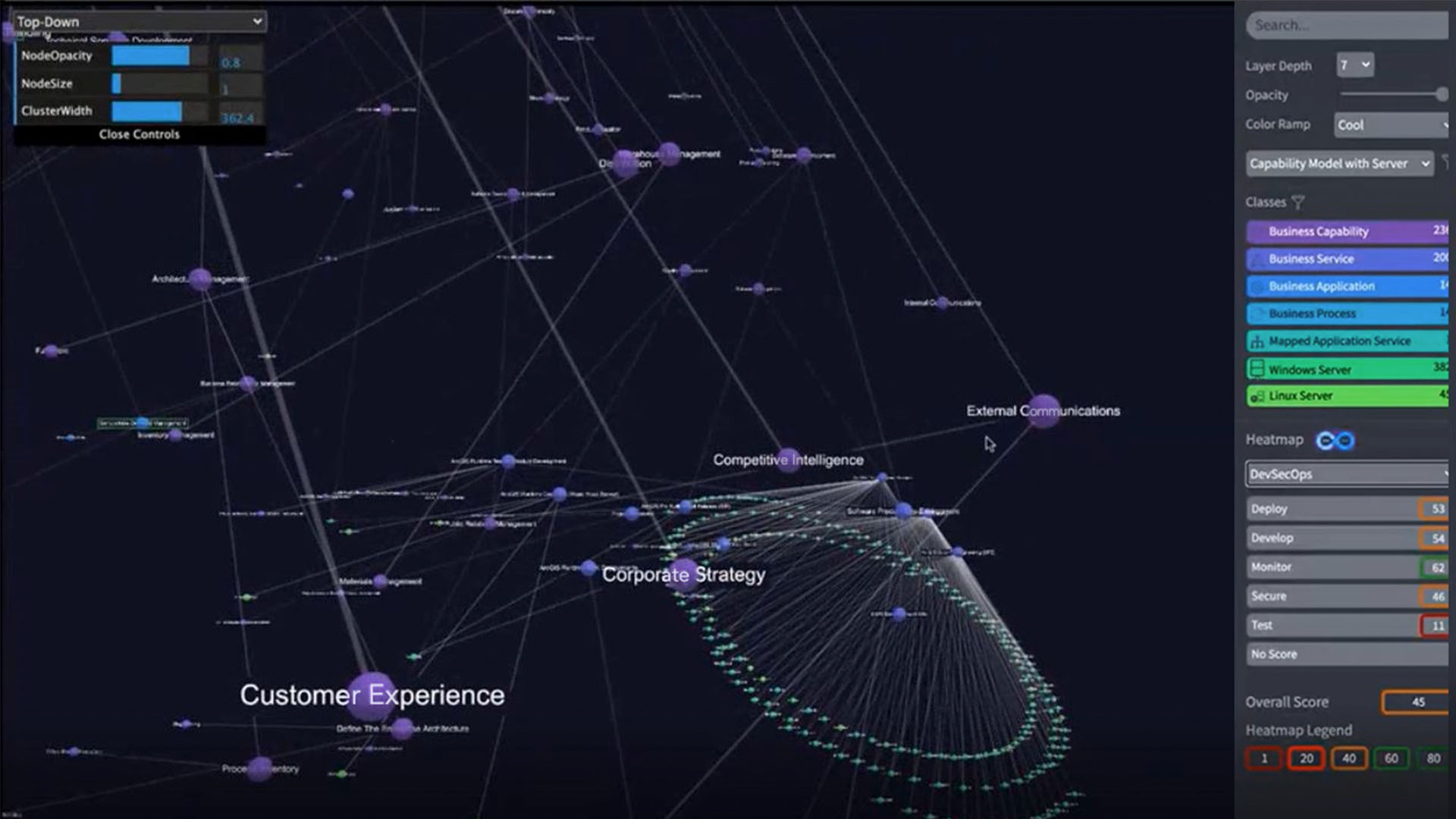
Dan Abushanab: It all starts with our CMDB, or our configuration management database. IT people know getting a good and accurate CMDB is kind of the holy grail of IT. It’s something we’ve chased for a long, long time. It’s an IT map of our organization—of the technology, of the applications, of the people, of the data—everything about our company and all the relationships between them. And getting that list, getting that inventory really set and clean—it’s the start of everything else that we try to do now. You want to secure the organization, you want to manage risk, you’ve got to have an inventory of what it is that you’re trying to manage. You can’t really manage what you can’t see.
Chiappinelli: That’s a good point. What has changed in that equation recently? What’s new?
Abushanab: Well, probably the biggest difference is just in the number of applications we use, the amount of data that we track, the number of devices in our lives. Our CMDB has more than five million items in it, so it’s a big, big list of stuff.
The second big change, and unfortunately, I don’t think this is going to end any time soon, is the risk of bad actors is just continuing to get worse and worse. So, managing security risk over a larger and larger complex landscape is really what’s different.
Chiappinelli: So, you’ve got this IT map concept to visualize things. Where does location intelligence or location technology fit into the picture?
Abushanab: Our CMDB, our IT map, has in it—on all the items where it makes sense—we have a location on there. So, a physical piece of gear or a person’s workplace. And so, consequently, we can show that in a GIS [geographic information system] and we can look at work that we’re doing through a geographic context.
A couple examples. One is just making sure that the list is right, just making sure the data we have in the CMDB is right. When I look at that through a map, I can send someone from the Denver office and say, “Go look at the CMDB in Denver and make sure that things look right to you, that it passes a sniff test.” That’s one example, just validating the information, building trust in the information. Because we won’t use it if we don’t trust it.
The second thing is when we’re trying to do a project, some projects’ location is a part of them. Like, when we wanted to upgrade our firewalls or we wanted to upgrade our MPLS network, those projects lend themselves to looking at the work through a geographic context because you have to do it in a lot of different places. So, that’s another way that the IT map, partnered with the GIS, comes into play.
Then the third way, I think, is when there’s something gone wrong. Let’s say you have a critical patch or an outage related to an operating system, so thousands of machines across your company are in need of attention. We do that through automation. But then we can use the map to look at, “How successful were we?” And if we see pockets where it looks like we didn’t get the automation into that corner of the company for whatever reason, we can send someone out to look at that. So, we can use tools in GIS to assess and do a better job of remediation as well.
Chiappinelli: You’re starting to allude to this, but what kind of benefits come from this if a CIO is using an IT map?
Abushanab: Well, like I said earlier, you can’t manage what you can’t see, right? So, our jobs in IT are to be boring, is the way we talk about it. I don’t want people thinking about the IT environment. I want them using it, but I don’t want them worrying about it. I just want to make things run really, really smoothly. I can’t do that well if I don’t have my arms around what I’m dealing with, if I’m not managing risk, if I’m not recovering from events in a quick and timely way. And my IT map helps me do all of that better.
Chiappinelli: Excellent. Well, that’s a lot for folks to think about. It’s a very fascinating concept. We certainly thank you for your perspective, Dan.
Abushanab: Thanks, Chris. Nice to be here.
Chiappinelli: If you’re curious about any of the concepts we talked about or that you saw on the screen, check out the link in the article and that’ll give you a little bit more information about the IT mapping concept and how it all comes together. For the WhereNext Fast Four, I’m Chris Chiappinelli. Thanks for being with us, and we’ll see you next time.
The Esri Brief
Trending insights from WhereNext and other leading publicationsTrending articles
December 5, 2024 |
July 25, 2023 |

April 1, 2025 |
November 12, 2018 |

November 25, 2024 |

April 16, 2024 |