The annual cost of cybercrime is expected to exceed $8 trillion by the end of this year, according to research company Cyber Ventures. To mitigate the consequences of cybersecurity attacks, cybersecurity teams continually evaluate and develop creative methods for response and preparedness. Advances in surveillance, detection, and analysis can serve as a force multiplier for the many outnumbered, task-saturated crews that are charged with protecting software and technology.
ArcGIS AllSource, Esri’s new intelligence software, facilitates investigative, geospatial, and link analysis. AllSource can be used in all phases of the cyber threat intelligence cycle, from developing an understanding of the threat and collecting, processing, and analyzing data to disseminating the results and gathering feedback. AllSource enables users to leverage the advanced analytics of ArcGIS Enterprise along with ArcGIS Knowledge to identify threat vectors and deploy mitigation strategies that protect an organization’s cyberinfrastructure.
Take a tour of the six steps that cybersecurity teams typically use to find and study adversaries’ tactics, techniques, and procedures. Using a right-to-left override attack—which tricks people into clicking malicious text files—as an example, find out how AllSource helps put defense strategies in place and evolves with the complexity of each threat.
-
Determine Appropriate Actions to Take
All stakeholders within an organization must be able to gain a clear and specific understanding of the potential impacts of a cybersecurity compromise, as well as their role in preventing one. AllSource can serve as the starting point from which a cybersecurity program grows by allowing analysts to, first, record the attack methods, known attackers, and organizational infrastructure that should all be prioritized.
It is essential to identify what an organization needs to protect, such as networks, physical assets, customer data, and trade secrets. From there, the organization’s cybersecurity team can develop and implement a threat intelligence strategy. This ensures that all team members understand the organization’s key priorities and allows them to mount a highly responsive defense in reacting to or preventing an attack.
-
Collect Data on Threats
When cybersecurity analysts detect activity based around a certain threat vector—the way an adversary can breach or infiltrate a network or system—they can use AllSource to investigate the threat and set in motion a series of steps to preemptively mitigate an attack.
During a right-to-left override attack, analysts can import data into AllSource and make connections to sources such as the MITRE ATT&CK framework, an openly accessible knowledge base of cyberattack tactics and techniques. They can then layer in threat information and operational data and use the link analysis tools, graphs, and timelines in AllSource to see patterns in the attack and gain insight into the situation.
-
Process the Threat Data
Once data sources are mapped and information flows into AllSource, it is typically necessary to normalize the data for use within the enterprise.
The MITRE ATT&CK dataset, for instance, offers many ways to access the data, including as a JavaScript Object Notation (JSON) file, a Python library, or a Microsoft Excel workbook. The tools available in AllSource help analysts prepare and clean the data so that it’s easier for others to use.
Say the MITRE ATT&CK dataset is downloaded as an Excel workbook. An analyst would import each sheet into a mobile geodatabase within AllSource to ensure that all the field types are correct and allow for a more robust analytical experience. Using the Convert Time Field tool, for instance, the analyst could change many field types to a date field (or a text or numeric field). This would give the organization clean, usable MITRE ATT&CK data in a mobile geodatabase that can be shared or set as a local copy.
-
Analyze and Present the Data
With the data prepared for use, analysts can leverage the advanced analysis functionality provided by the back-end ArcGIS Knowledge Server site deployed within ArcGIS Enterprise to get a deeper understanding of the threat vector—in this case, the right-to-left override.
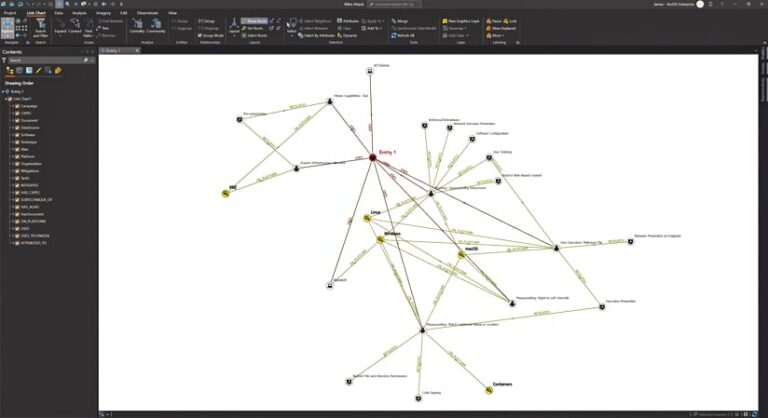
An analyst would drill down further into the data to discern the number, cadence, and location of similar attacks that have been reported—both within the organization and from other organizations—over a specified period. Expanding the resultant knowledge graph from the MITRE ATT&CK dataset within AllSource, the analyst could detect a handful of organizations that are prone to this kind of attack. The analyst could then pinpoint particular threat vectors and see that Entity 1 tends to use these threat vectors. If the analyst selects Entity 1 within the knowledge graph, they could see that it is a terror organization.
Through the relationships that are established in the knowledge graph, it would appear that Entity 1 is known to employ additional threat vectors in its attacks. Using AllSource, the analyst could identify such attacks and determine the best steps to take to mitigate them. Seeing that Entity 1 matched well with the description of activities found in open-source intelligence collections, the analyst could also make recommendations with a marked level of confidence for how to allay the effects of such an attack and bolster their organization’s security posture.
-
Disseminate Analysis Results
Once all the relevant data has been analyzed, analysts can generate reports directly within AllSource with recommended mitigation actions that show the way forward. This gives stakeholders and decision-makers the full scope of the operational landscape in which the cybersecurity team is operating.
Analysts can also easily share critical information with other analysts as feature services, web maps, layouts, reports, and layer and project packages. This gives them access to the source data, allowing anyone working on a team or across shifts to conduct their own research and continue threat mitigation or response efforts. It enables cybersecurity teams to set mitigation actions and take additional measures to prevent or insulate their organization’s architecture from follow-on attacks.
-
Get Feedback
To ensure that an organization’s security posture evolves with an ongoing threat and takes new ones into consideration, cybersecurity teams continually analyze the efficacy of their responses to attacks, as well as their efforts to prevent them and lessen their severity when they do happen. In a postaction session, stakeholders can use AllSource to capture critical insight and adjust mitigation steps accordingly to make certain that any new requirements in defensive tactics are captured and cataloged.
The sheer volume of data that’s available to support cyber threat intelligence operations can be overwhelming. AllSource helps cybersecurity teams make sense of that data by extracting pointed intelligence from it and bringing context to suspicious activities.
Learn more about ArcGIS AllSource. Current Esri users may also contact their Esri representatives.

